React2Shell is a critical vulnerability, with a CVSS score of 10 out of 10, that allows remote code execution (RCE) without authentication. It affects web applications that use React Server Components and the Next.js framework.
Besides the name "React2Shell", this vulnerability is also known as:
• CVE-2025-55182 for React.
• CVE-2025-66478 for the Next.js framework
Now, if you are wondering if your web application is vulnerable to it, this article provides some methods to determine this:
Using the React2Shell Scanner
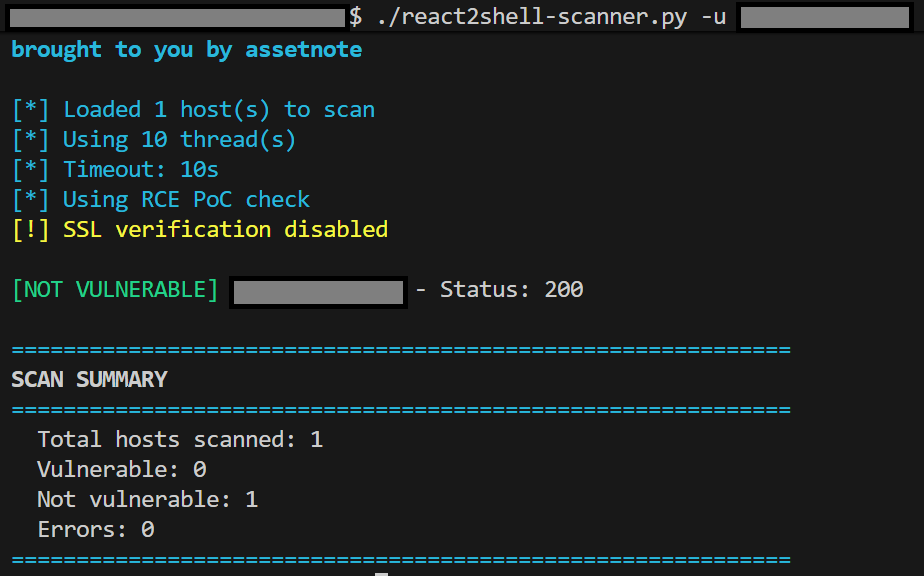
This simple method requires no login to the server that hosts the website. It uses React2Shell Scanner, a Python script that connects to a website, and determines whether it is vulnerable to React2Shell or not. While other similar tools and PoC exist, this one can be deemed reliable, as it follows the methodology thoroughly described on this page.
Prerequesite: a computer able to run Python code. The example usages below assume you are using Linux or a unix-based operating system.
Disclaimer: this method is for preventive and educational use only. Only use it on your own website to determine if it is vulnerable and needs to be patched.
- Start by downloading or cloning the react2shell-scanner repo
- Try starting the scanner.py script. If it fails due to missing dependencies, you can install them using the provided
requirements.txtfile:
pip install -r ./requirements.txt
- Then, check your website using this command:
./scanner.py -u https://your.domain.ext
- The result is provided as output, indicating either "[NOT VUNERABLE]" or "VULNERABLE"
By reviewing the packages used by your web application
Here is a list of the vulnerable packages. If you use one of them, your application is likely to be vulnerable and you need to upgrade to the indicated fixed version:
| Vulnerable Components | Vulnerable Versions | Fixed Versions |
|---|---|---|
| react-server-dom-webpack | 19.0.0 19.1.0 – 19.1.1 19.2.0 |
19.0.1 19.1.2 19.2.1 |
| react-server-dom-parcel | 19.0.0 19.1.0 – 19.1.1 19.2.0 |
19.0.1 19.1.2 19.2.1 |
| react-server-dom-turbopack | 19.0.0 19.1.0 – 19.1.1 19.2.0 |
19.0.1 19.1.2 19.2.1 |
| Next.js | 15.0.0 – 15.0.4 15.1.0 – 15.1.8 15.2.0 – 15.2.5 15.3.0 – 15.3.5 15.4.0 – 15.4.7 15.5.0 – 15.5.6 16.0.0 – 16.0.6 |
15.0.5 15.1.9 15.2.6 15.3.6 15.4.8 15.5.7 16.0.7 |
| Next.js | 14.3.0-canary.77 and later canary versions | Downgrade to the latest stable 14.x release by running npm install next@14 |
| Other Frameworks | Any framework/library that bundles the vulnerable React RSC implementation (e.g. Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, Waku) |